ICTTF - Ransomware Uncovered - Specialist Certificate
ICTTF - Ransomware Uncovered - Specialist Certificate
black swan event - is an unprecedented event that becomes quite normal.
first ransomware - 1989 - name ATOS
malvertsiging
LOCK - 2016 > load to memory > delets itself > encrypt storage by pattern > encrypt network storage > delte volume snapshots > change wallpaper
bitcoin for payment
ransomware as a service
Dodge bullet - 2017
there is ransomew for - Mobile device - PC - TV - IOT
CONTI - HSE - Ransomware - they offer proof of life
How to defend againt ransomware ?
rveryone need to take care for their enviroment

Talk to the board
anti virus / edt - installed up to date and monitored
Need to do cyber risk assesment
Cyber Hygiene
- Scan Emails
- Firewall Config
- Endpoints
- Notify Users - Emails
- Segmentation
- Offline Backups - 3 Types
- Protect Information
- Patch Management
How to Respond
- Don't Panic
- Use do not encrypt
- Know your policy and coyer insurance
Tips
- Isolate Systems - Pull the cable out
- Identify the malware
- Involve authorities
- Involve experts
- Remove the malware
- Recover with decryption
- Recover data from backup
- Prevent further
What is the primary motivation of cyber criminals?
Money
Generally what level of skills do state sponsored threat actors have?
Very high
Underground Economy of Cybercrime: Who are the "People Persons"?
Organisational Leaders
A type of malicious software designed to carry out or facilitate illegal online activity is called?
Crimeware
The Fifth Domain Refers to Warfare on What Front?
Cyber Space
The network of physical objects—a.k.a. "things"—that are embedded with sensors, software, and other technologies for the purpose of connecting and exchanging data with other devices and systems over the Internet
IoT - Internet of Things
A stealthy surgical cyber threat actor, typically a nation state or state-sponsored group, which gains unauthorised access to a computer network and remains undetected for an extended period.
APT - Advanced Persistent Threat
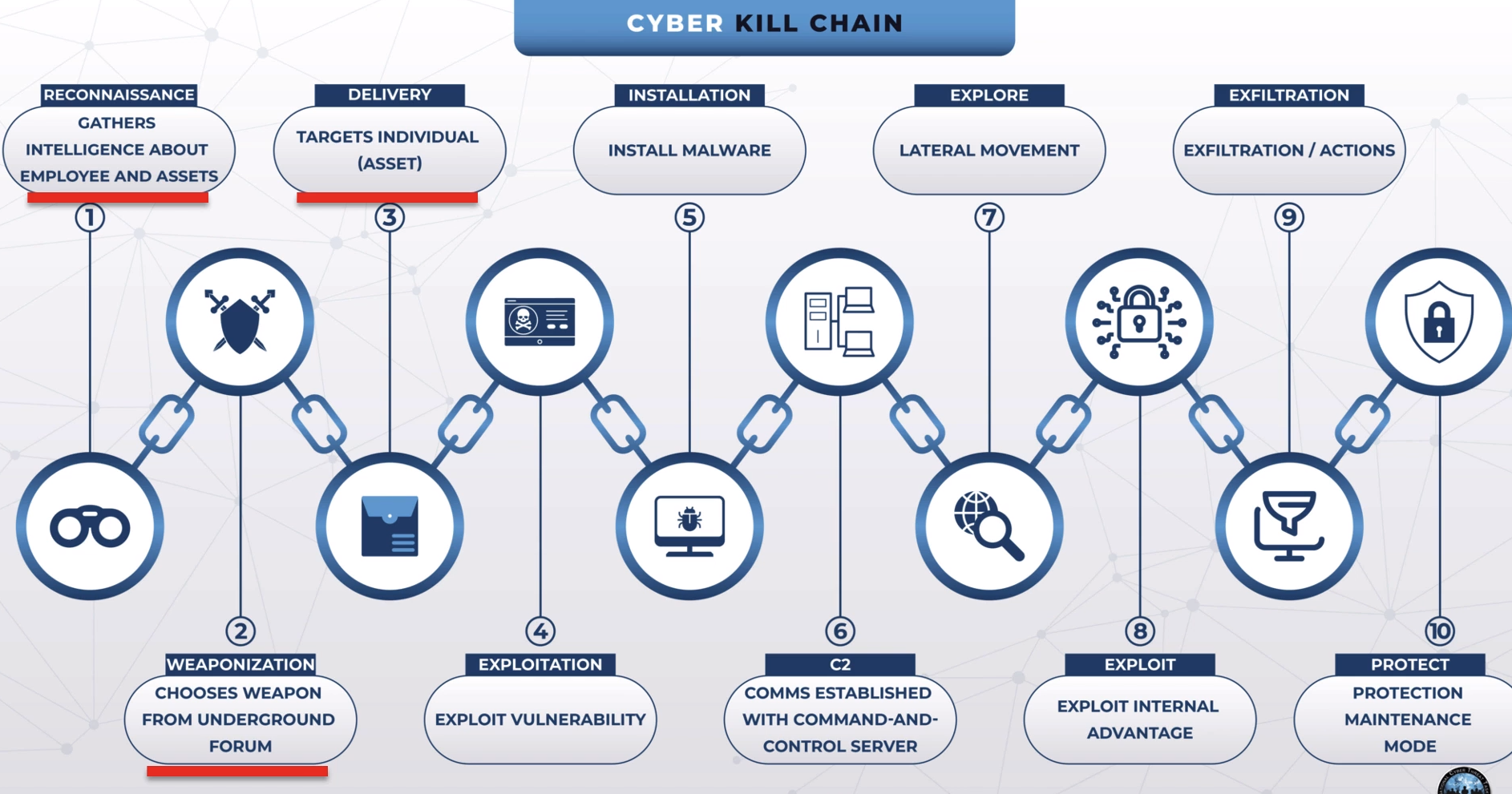
Stage 10 of the Cyber Kill Chain
Protect
The Year of the First Ransomware - AIDS
1989
The Three Main Delivery Channels of Ransomware (Select 3 Answers)
Phising
Malvertising
Drive by infection
The process of encoding information. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext.
Encryption
A digital asset designed to work as a medium of exchange wherein individual coin ownership records are stored in a ledger existing in a form of a computerized database using strong cryptography to secure transaction records, to control the creation of additional coins, and to verify the transfer of coin ownership. Example Bitcoin
Cryptocurrency
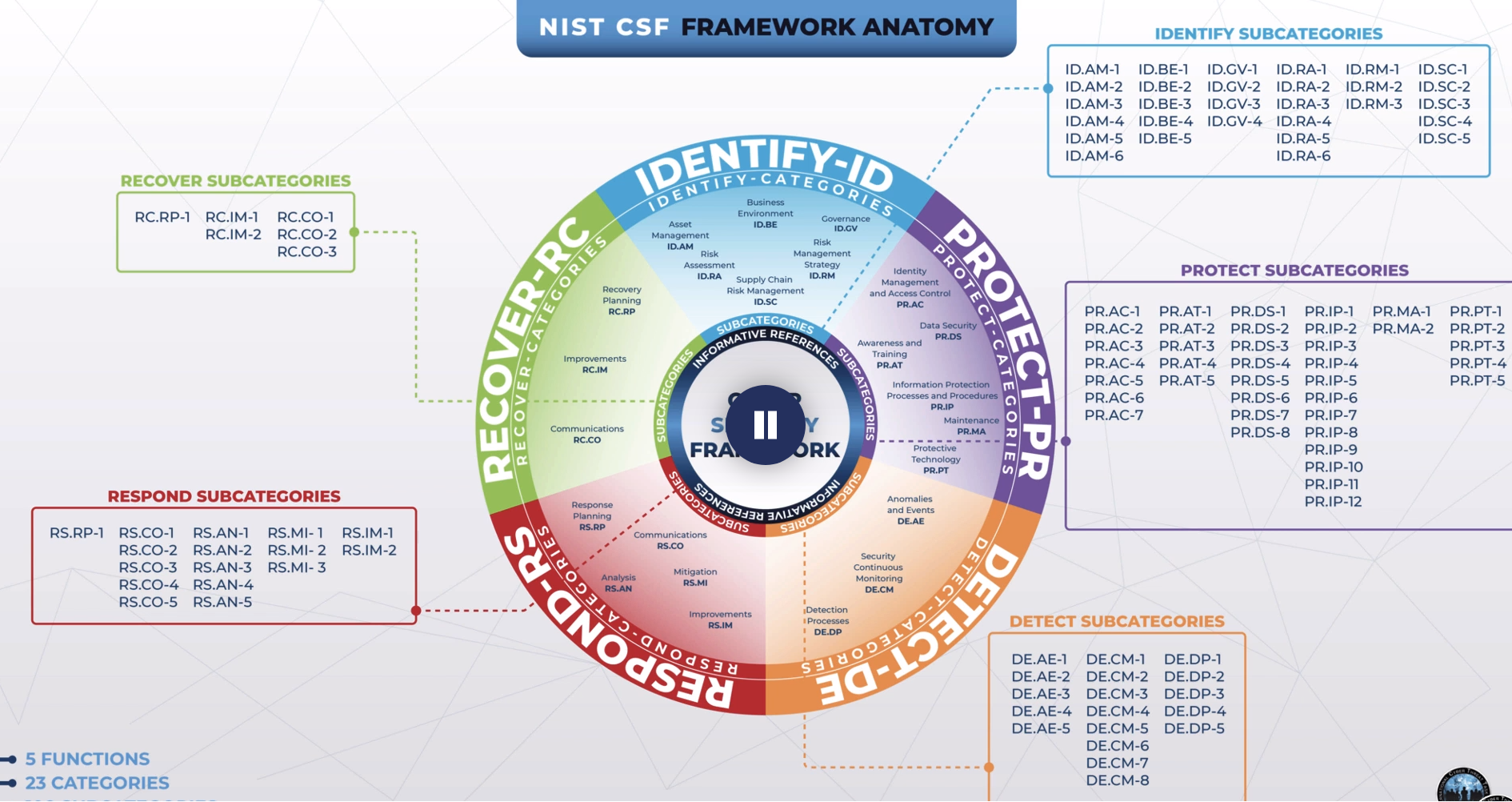
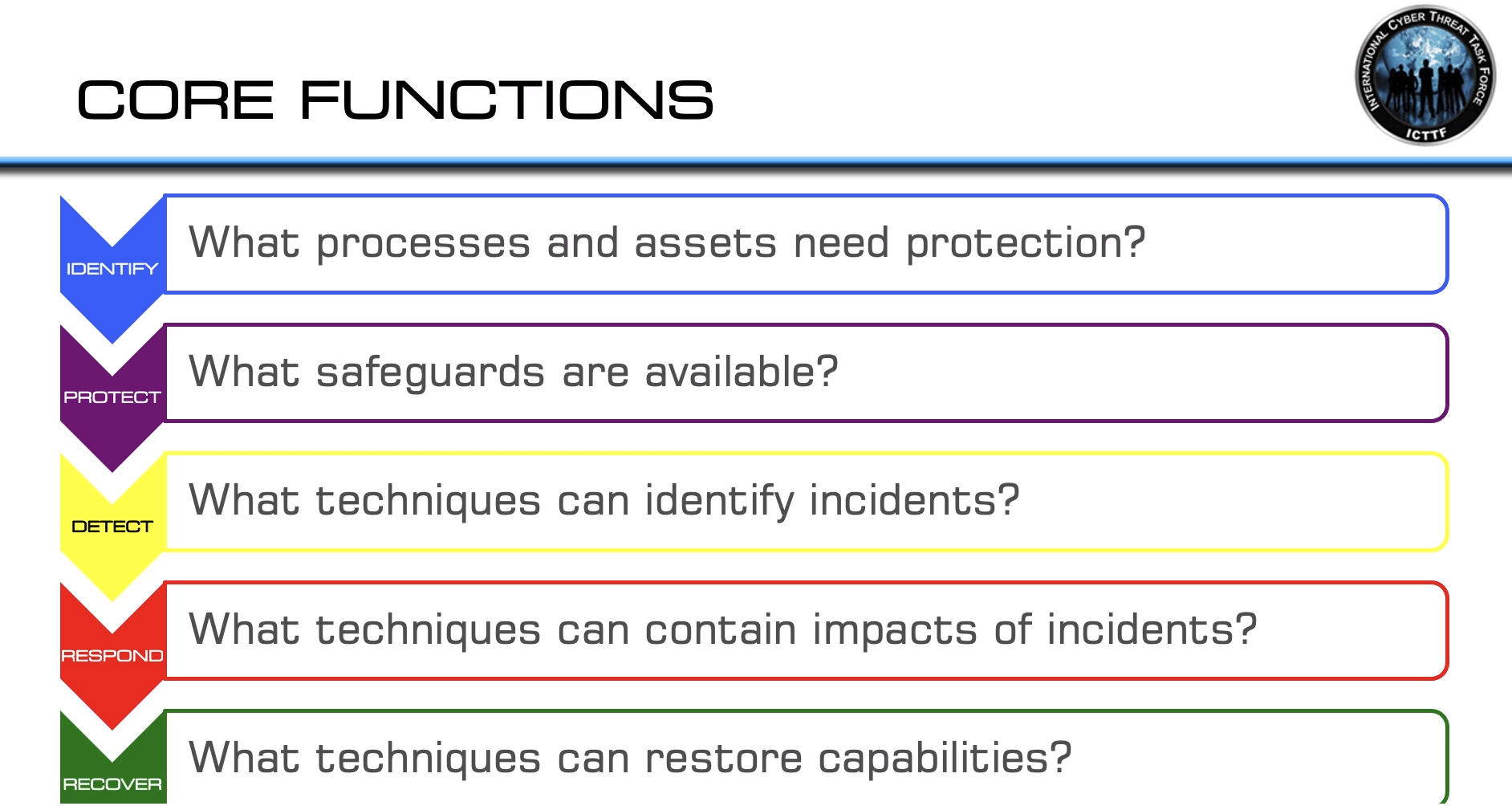
The Number of Functions in the NIST Cyber Security Framework
5
Name the NIST Function: What techniques can contain impacts of incidents
Respond
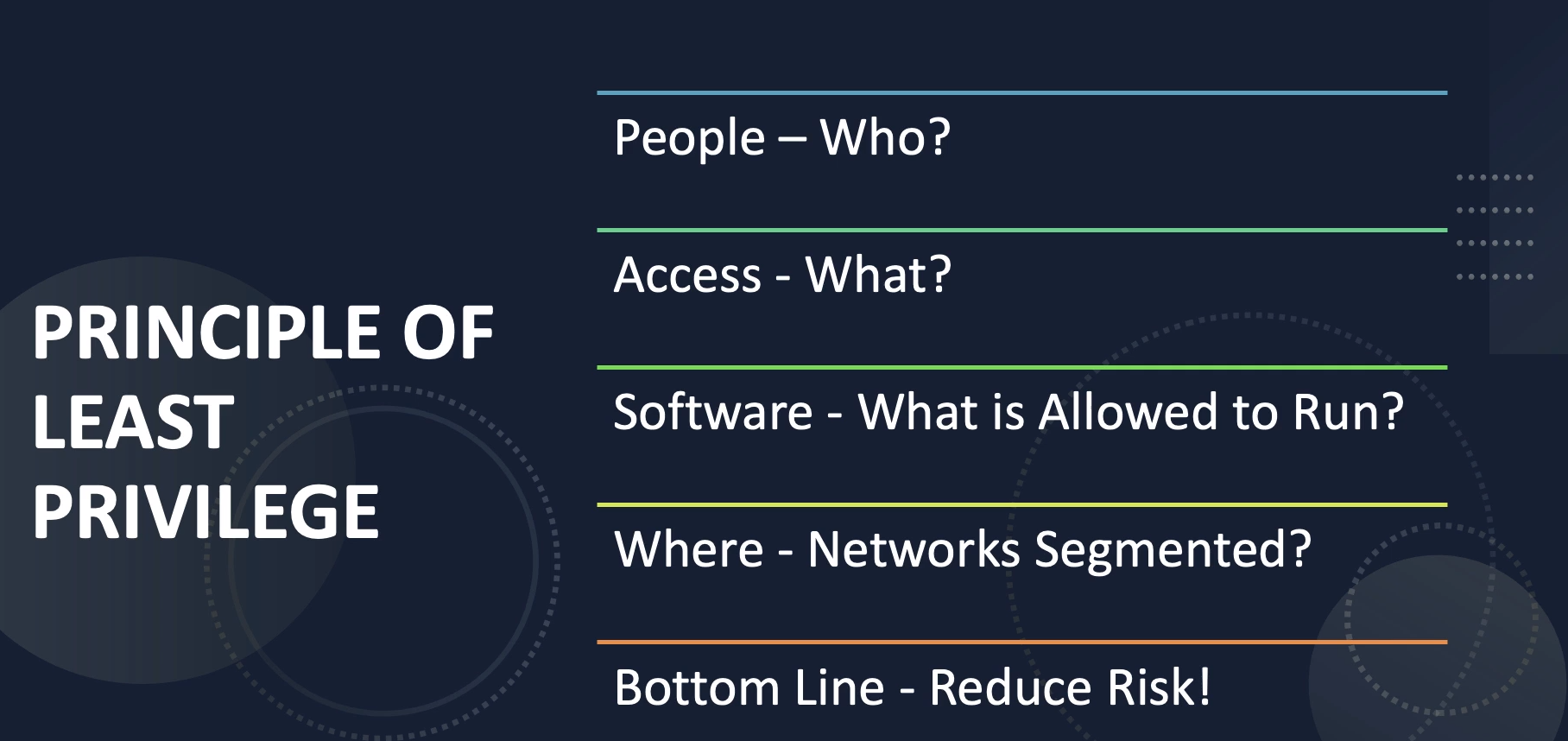
An information security concept in which a user is given the minimum levels of access – or permissions – needed to perform his/her job functions.
The principle of least privilege (PoLP)
A Cyber Hygiene Tip
Patch
Ransomware Response Tip
ID The Malware
The act or practice of splitting a computer network into subnetworks, each being a network segment.
Network Segmentation
The Web Address for the "No More Ransom" Project
www.nomoreransom.org
What you should NEVER do if you are the victim of ransomware
Panic